New Mobile Backend authentication
Overview
It is needed to find a way to replace the current login flow and authenticate calls to Mobile Backend using Auth0 authentication.
Proposals
Option 1: Remove login mutation and send Auth0 access token in request authorization header
Mobile App will stop calling login mutation to authenticate the customer, Auth0 access token will be send on each request to the Mobile Backend in Authorization header.
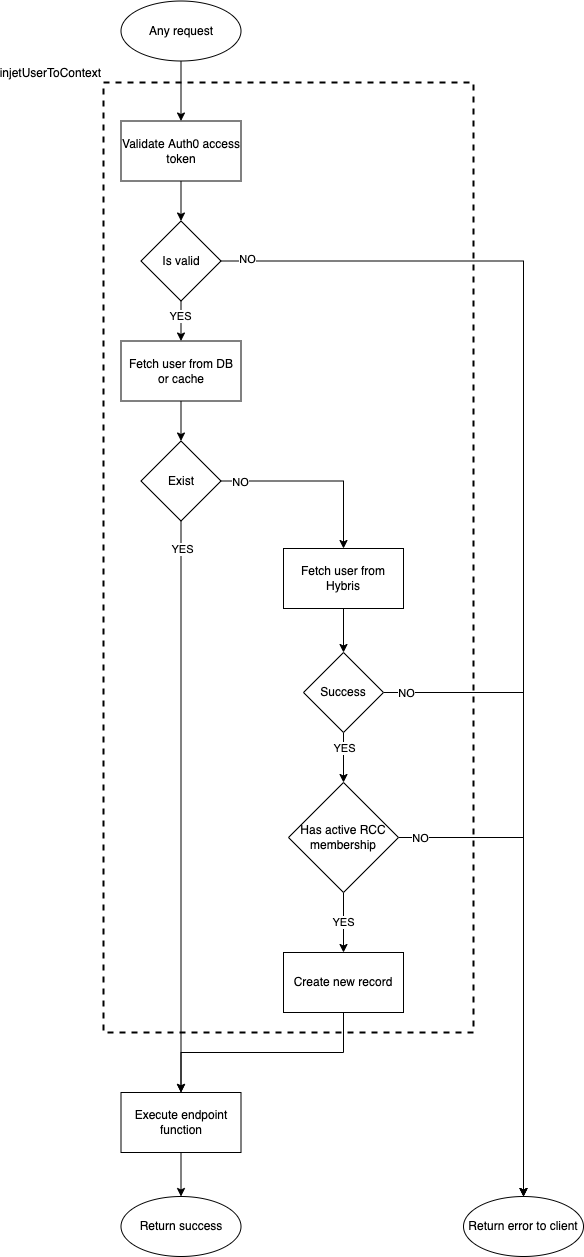
injetUserToContext needs to be modified to validate Auth0 access token instead of old JWT one and load Auth0 customer metadata.
In case the token is invalid for Auth0 it should throw an error as it is currently done in login mutation.
If the customer doesn't exist in Mobile Backend database, he will be created in the same way as now, fetch data from Hybris and validating his RCC membership.
Advantages
- Validate customer only against Auth0 and not have the need of managing Backend Mobile JWT token.
- Mobile App needs only to store Auth0 tokens.
- Customer is validated against Auth0 on each call.
Disadvantages
- Customer creation needs to be done in
injetUserToContextstep, it isn't a separated action. - RCC membership is only validated by
validateMembershipwhen creating a customer? not sure if this is right. - Customer data is never updated from Hybris as including this in
injetUserToContextcan low the performance. It would require to call Hybris for customer details on each call to the Mobile Backend, instead of what is being doing now that is update the customer when the login mutation is called.
Notes
- Deprecate
verifyJWTfunction and verify token against Auth0 instead. ensureValidTokenneeds to be modified to validate Auth0 token.- How or when to update customer data in Mobile Backend database? Currently it is being done in login mutation but after this changes customer update is never done.
Option 2: Send Auth0 access token in request authorization header and create new endpoint to create/update users
Mobile App will stop calling login mutation to authenticate the customer, Auth0 access token will be send on each request to the Mobile Backend in Authorization header.
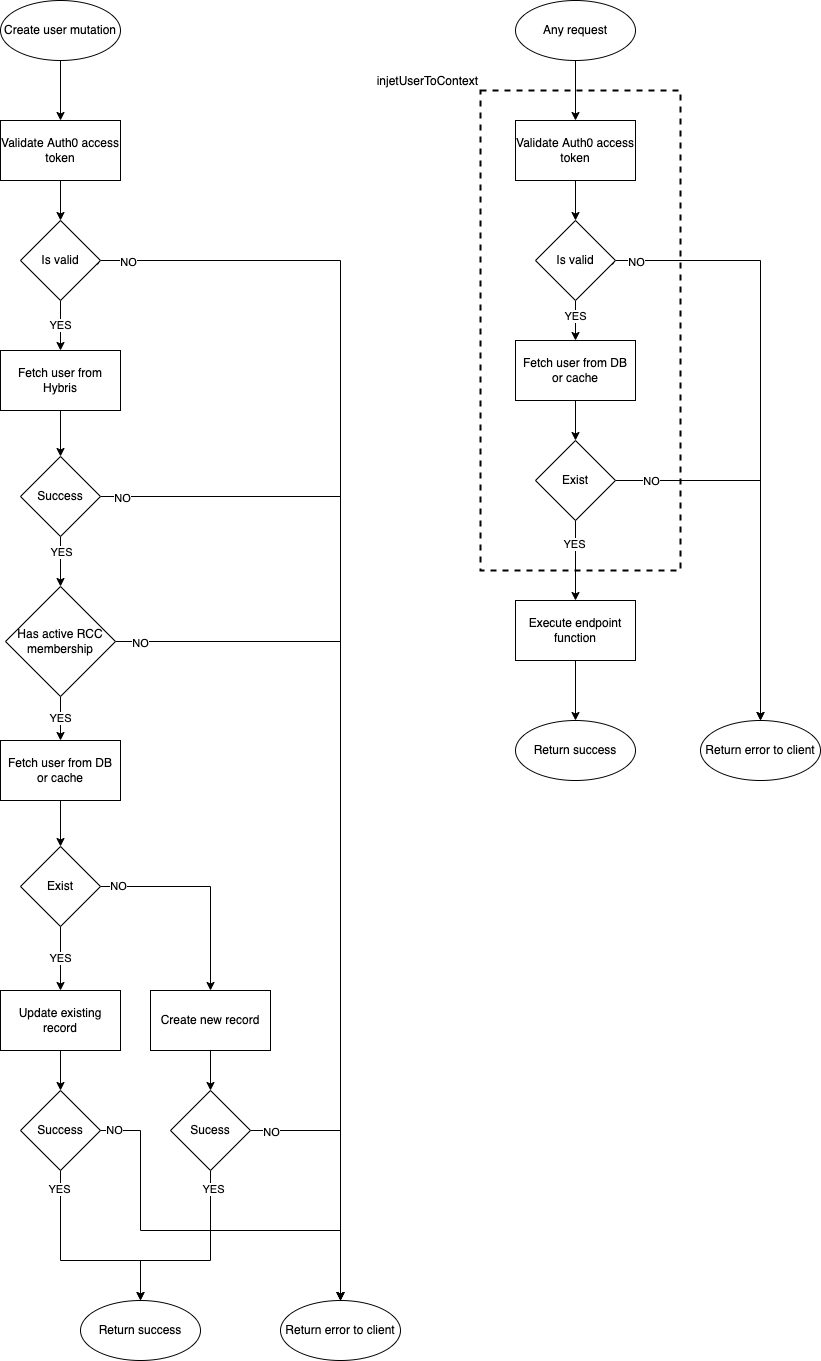
injetUserToContext needs to be modified to validate Auth0 access token instead of old JWT one and load Auth0 customer metadata.
In case the token is invalid for Auth0 it should throw an error as it is currently done in login mutation.
Unlike option 1, the customer won't be created by injetUserToContext, the proposal is to create a new mutation to create or update users.
Create customer mutation will replace login one, the difference will be that it won't generate JWT token and it will accept Auth0 access token instead of customer username and password. It will get Hybris customer data, check his RCC membership and create or update the customer in Mobile Backend database in the same way that the login process does it now.
If it is a new customer, Mobile App will need to create the customer with create user mutation before calling any other endpoint. If and endpoint is call and the user doesn't exist on the mobile backend, it will return an error.
Advantages
- Validate customer only against Auth0 and not have the need of managing Backend Mobile JWT token.
- Mobile App needs only to store Auth0 tokens.
- Customer is validated against Auth0 on each call.
Disadvantages
- Mobile App needs to call new create customer mutation instead of login mutation in order to create or update the user.
Notes
- Deprecate
verifyJWTfunction and verify token against Auth0 instead. ensureValidTokenneeds to be modified to validate Auth0 token.
Option 3: Keep mobile backend login but accept Auth0 access token instead of username and password
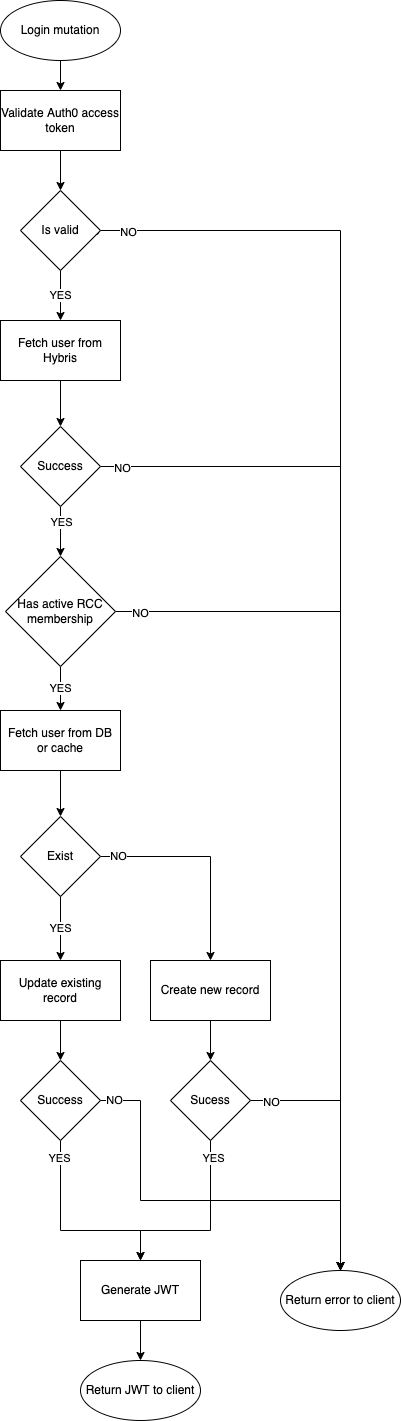
Mobile App will continue calling login mutation, but now the call should be done with Auth0 access token instead of customer username and password.
Login mutation should validate Auth0 token and get Auth0 user's metadata in order to update the data stored in the database or create a new user, then it will return a JWT token as it is done now.
The JWT token will be used in authorization header to call Mobile Backend endpoints as it is being done now.
Advantages
- Keep most of the Mobile Backend working without changes, just update login mutation.
Disadvantages
- Mobile App will need to store both new Auth0 tokens and Mobile Backend JWT token.
- Customer authentication against Auth0 will be performed only once, then the Mobile Backend will trust on the generated JWT as it does now.
Notes
- Regardless of choosing one proposal or another, current calls to Hybris are being made with a token obtained with grant type
client_credentials. Does it make sense to change it to use a token generated with grant typepasswordand customer's credentials? (The Hybris token saved in Auth0 on each user) - In order to be able to validate the customer against Auth0, the customer needs to be previously migrated to get his
uidfrom Auth0 customer metadata. It is needed to check if the customer login in Mobile App also triggers Auth0 login migration action.
⚠️ In the meantime that we are migrating customers we will need to keep login mutation and JWT authentication still working along with new proposal. (Proposal to avoid this issue)
This is because Auth0 login migration action will need to call login mutation with customer username and password in order to get access to Mobile Backend.
Once the migration is completed we can disable or delete login mutation.